DATA SECURITY ENGINE

Darkstrike Halo™ — a client-controlled zero-compromise data security engine for ransomware and quantum-ready data protection.
CLIENT-CONTROLLED
Data Security.
Engine.
Darkstrike Halo™ is a data security core for enterprises that want control over their own data storage. It delivers the same ransomware and quantum-ready protection used in our fully hosted model, Darkstrike Dome™. Darkstrike Halo™ offers flexibility and data sovereignty for a wide range of use cases.

Client hosts data & blueprints
Client manages data security core
Client manages data security core
ON-PREM

Client hosts data & blueprints
Darkstrike™ manages data security core
Darkstrike™ manages data security core
SELF-HOSTED

Client hosts data
Darkstrike™ manages data security core & blueprints
Darkstrike™ manages data security core & blueprints
HYBRID
ON-PREMISE SOVEREIGN SECURITY
Halo Elite™
On-prem.
Darkstrike Halo™ Elite is our on-prem solution for government, military, and approved corporates requiring full data and security control. It combines maximum sovereignty with advanced ransomware and quantum-ready protection — ideal for high-compliance environments.

Product Brief.
View the Darkstrike™ Product Brief for an overview of our secure data architecture, deployment models, and capabilities.

We protect your data against the bad guys.
SELF-HOSTED PROTECTION & MANAGED ENCRYPTION
Halo Pro™
Self-hosted.
Darkstrike Halo™ Pro is our self-hosted model for clients who want to store data on-prem while leveraging Darkstrike’s advanced encryption and data restructuring. You control the storage — we handle the protection, including post-quantum encryption of restructured data.
HYBRID CONTROL & MAXIMUM ASSURANCE
Halo Standard™
Hybrid.
Darkstrike Halo™ Standard, our hybrid model, allows clients to maintain full control over their data while relying on Darkstrike to manage encryption operations and storage of data reconstruction artifacts. Darkstrike Halo™ Standard delivers the best of both worlds — the data sovereignty of a self-hosted model combined with the integrity of our fully-hosted model, Darkstrike Dome™.
CUSTOMIZABLE ENCRYPTION
Crypto Agile.
Each dataset can utilize quantum-secure or quantum-resistant encryption based on its confidentiality requirement.
QUANTUM-SECURE
Based on cryptography that is mathematically unbreakable — secure against quantum computers. Gold standard for future-proof security.
Security is mathematically unbreakable, regardless of an attacker’s time and power.
Does not utilize security dependent on encryption complexity.
Protects against any adversary with unlimited time and power.
Protects against any adversary with limited time and power.
Protects data from ransomware attacks and attenuates ransom claims.
Protects data from harvest now, decrypt later attacks.
QUANTUM-RESISTANT
Based on post-quantum cryptography with high computational difficulty — resists quantum attacks. Strong now but could have future vulnerabilities.
Does not utilize security that is mathematically unbreakable.
Encryption complexity increases difficulty for adversaries with limited time and power.
Encryption complexity is vulnerable to adversaries with unlimited resources.
Strong protection against adversaries with practical limits on time and power.
Provides varying protection dependent on implementation parameters.
Varying harvest now, decrypt later protection dependent on implementation parameters.
MODULAR ARCHITECTURE
Product comparison.
Below is a comparison of our data security solutions, Darkstrike Dome™, a fully-hosted, end-to-end data vault and exchange system, and Darkstrike Halo™, a client-controlled data security engine. Each solution provides all of our services.*
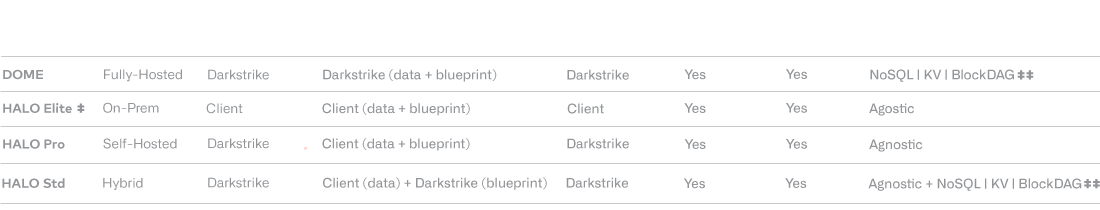
* Includes: Quantum-Ready Encryption · Ransomware Protection Service · Quantum Entropy Service · Quantum Key Generation Service · Quantum Data Exchange Service · Key Management Service
‡ Reserved for government, military, and certain approved corporates
‡‡ Future release
‡‡ Future release
15-day free trial.
Get a free demo of Darkstrike Halo™ for 15-days.
QUANTUM ADVISORY
Need help or guidance?
Our expert team will work closely with you to assess requirements, configure solutions, and provide necessary guidance for seamless implementation of our post-quantum cryptography (PQC) and ransomware protection services. Contact us to discuss how our professional services can support your specific needs.
Protect every byte.
Office Locations
Americas
108 Wild Basin Road South, Suite 250
Austin, TX 78746
555 Fayetteville Street, Suite 300
Raleigh, NC 27601
108 Wild Basin Road South, Suite 250
Austin, TX 78746
Raleigh, NC 27601
Europe
Kungsgatan 9
Stockholm
SE-111 43
Sweden
Kungsgatan 9
Stockholm
SE-111 43
Sweden
